Granting Oktually Access to your Okta
Allowing Oktually to read Okta data
Prerequisites
- A dedicated Okta account to act as the service account for Oktually
- You need to use an account with Super Administrator permissions for these steps, to be able to grant the Oktually service account admin roles
Create a Custom Role & Resource Group
Most of the access that Oktually needs is covered in the standard Read-Only admin role, but Oktually also needs some extra access to analyse data on administrators & API key usage.
Oktually will not have access to change administrators or see API key secrets (only their metadata)
- From the Okta admin dashboard,
Security→Administrators - Click on the
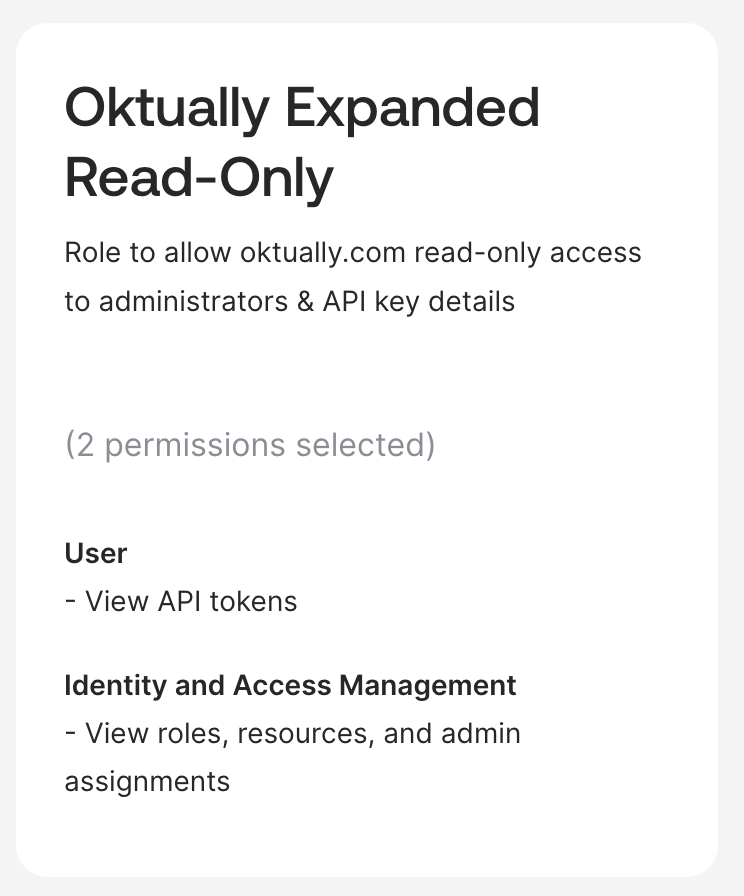
Rolestab Create new role- Give the role a name & description, for example
Oktually Expanded Read-Only&Role to allow oktually.com read-only access to administrators & API key details - Add these two permissions to the role
- Navigate through
User→Manage Users→Manage API Tokensand selectView API tokens. This is permission to see which API tokens exist & when they were used etc. not the tokens themselves - Navigate through
Identity and Access Managementand addView roles, resources, and admin assignments
- Navigate through
- Check the selected permissions against this example
- Select
Save Roleto save the role and return to theAdministratorspage - Select
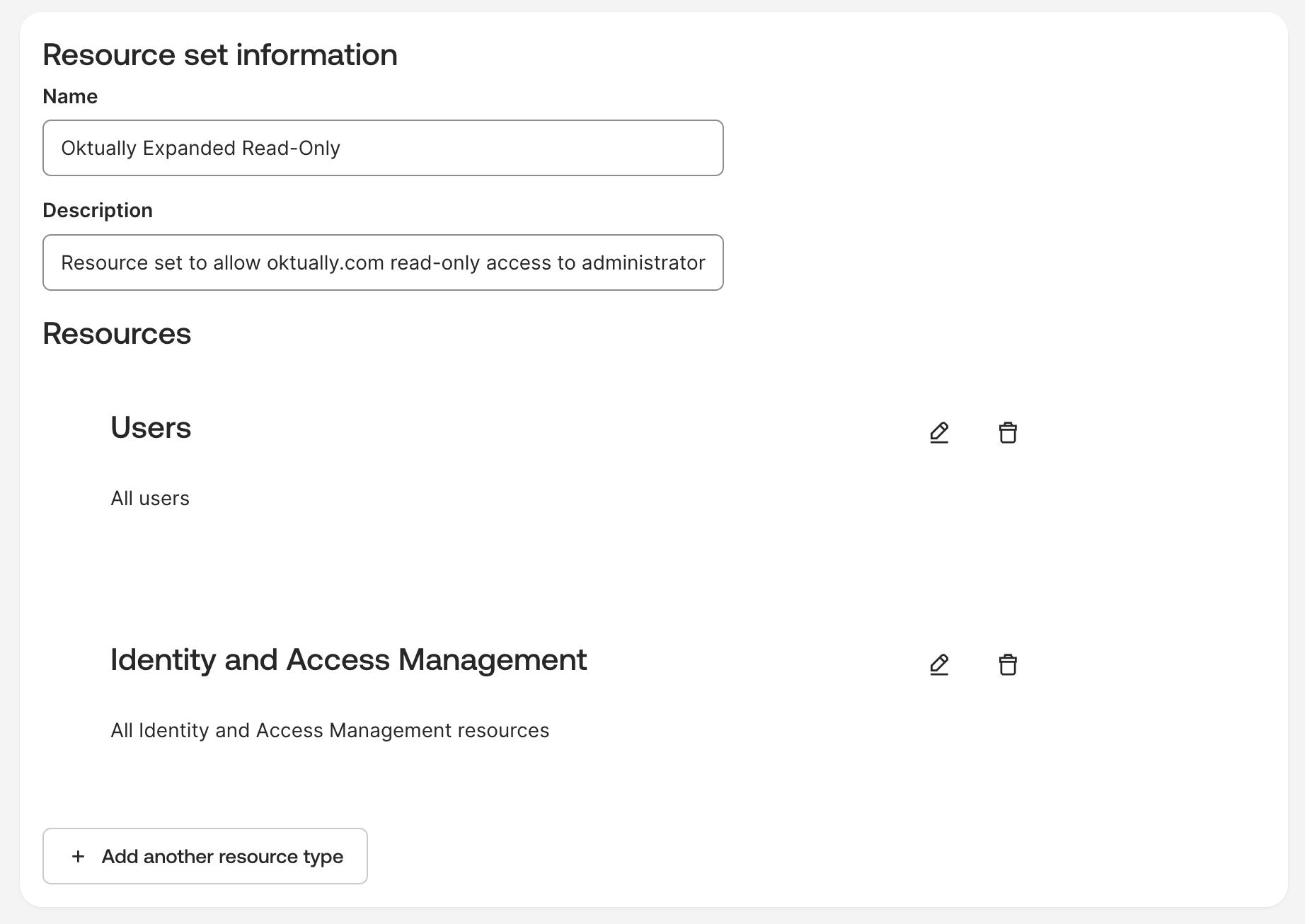
Resources→Create new resource set - Give the resource set a name & description, for example
Oktually Expanded Read-Only&Resource set to allow oktually.com read-only access to administrators & API key details - Add the following two resources
- From
UsersaddAll users - From
Identity and Access ManagementaddAll Identity and Access Management resources
- From
- Check the selected permissions against this example
- Save the resource set
Add Admin Permissions to the Service Account
- Open the profile for the Oktually service account, go to
Admin Rolesand selectAdd individual admin privileges - Add the following two assignments to the service account
- Role:
Read-Only Administrator - Role:
Oktually Expanded Read-Only(or your role name), resource set:Oktually Expanded Read-Only(or your resource set name)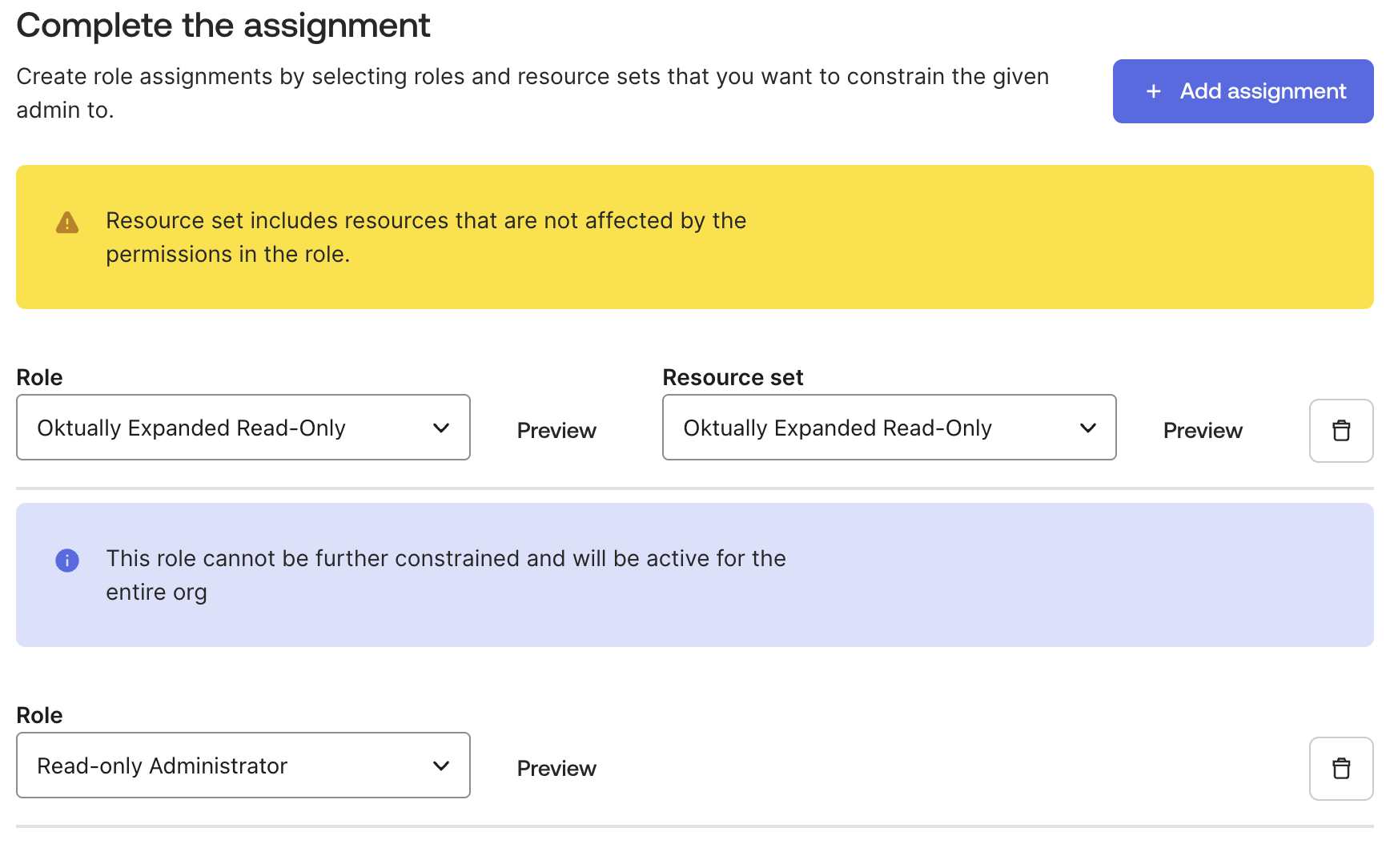
- Role:
- You’ll see a warning,
Resource set includes resources that are not affected by the permissions in the role.— this is expected. - Remember to
Save Changes
Create a Network Zone for Oktually (Optional, but Recommended)
- From the Okta admin dashboard,
Security→Networks Add Zone→IP Zone- Name the zone, for example
Oktually - In
Gateway IPsenter Oktually’s gateway IP, currently51.15.55.103/32 Savethe zone
Create Oktually’s API Key
Prepare your method of Sharing Secrets before creating the API key, so you can immediately submit the secret without storing it elsewhere.
- Sign in as the Oktually service account first, otherwise you’ll create an API key for your own admin account
- From the Okta admin dashboard,
Security→API - Select the
Tokenstab Create token- Enter a name for the API token, for example
Oktually Data Collection - If you created a network zone for Oktually:
- In
API calls made with this token must originate from, selectIn any of the following zones: - Select the zone you made for Oktually
- In
Create token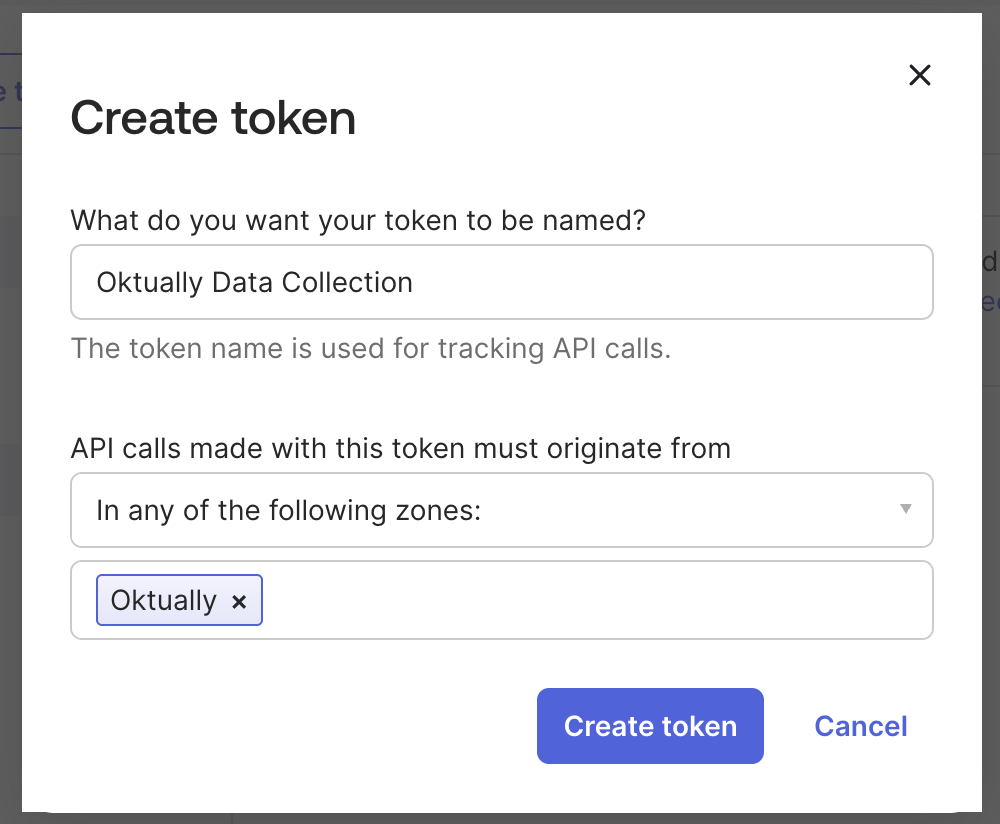
- Copy the
Token Valueand immediately submit it to Oktually via your chosen method for sharing secrets
Okta defaults API keys to 50% usage of each API’s rate limit. It’s your responsibility to set a limit which is high enough to allow Oktually to work, but not so high it impacts your Okta tenant.
A setting in the range of 25% to 75% is likely to work. Never set the Oktually API key’s limit to 100%