Detections
Motivation
- Okta’s event log is a mine of information, but you’ll never spot the important events manually
- The Detections tool is a reliable way to spot events likely to be worth investigating, without creating your own scripts, learning a query language or paying $$$ for a full SIEM
- This tool expands the capabilities of Oktually’s Event Timeline, by allowing detected events to be surfaced there for correlation and exposing the whole JSON log for review
- Traditional detections tend to focus solely on Okta’s log, whilst Oktually uses state data to refine broad detections down to those which matter most. Like Super Admins with new devices, new starter or C-Suite sign in problems and changes to groups you’ve told Oktually are important
Basic Usage
- Look for a detection of interest to you. Rows are colour formatted to indicate recency. Detections with the newest events will have more vivid colours
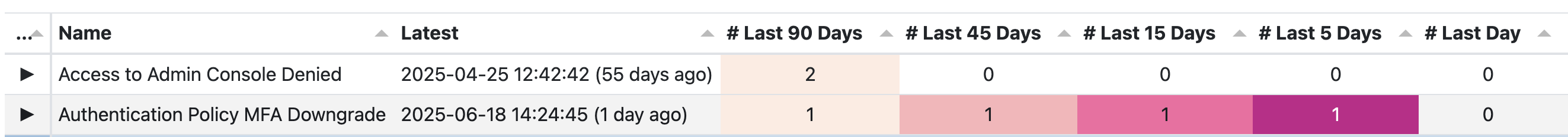
- Expand the row using the arrow on the left
- Open
Aboutto see information on the detectionEvent Timeline Linksto search the Event Timeline for detected events. Detected events will be marked with a star, rather than the usual diamond- More rows below to see up to 10 of the most recent full JSON logs, for each detection
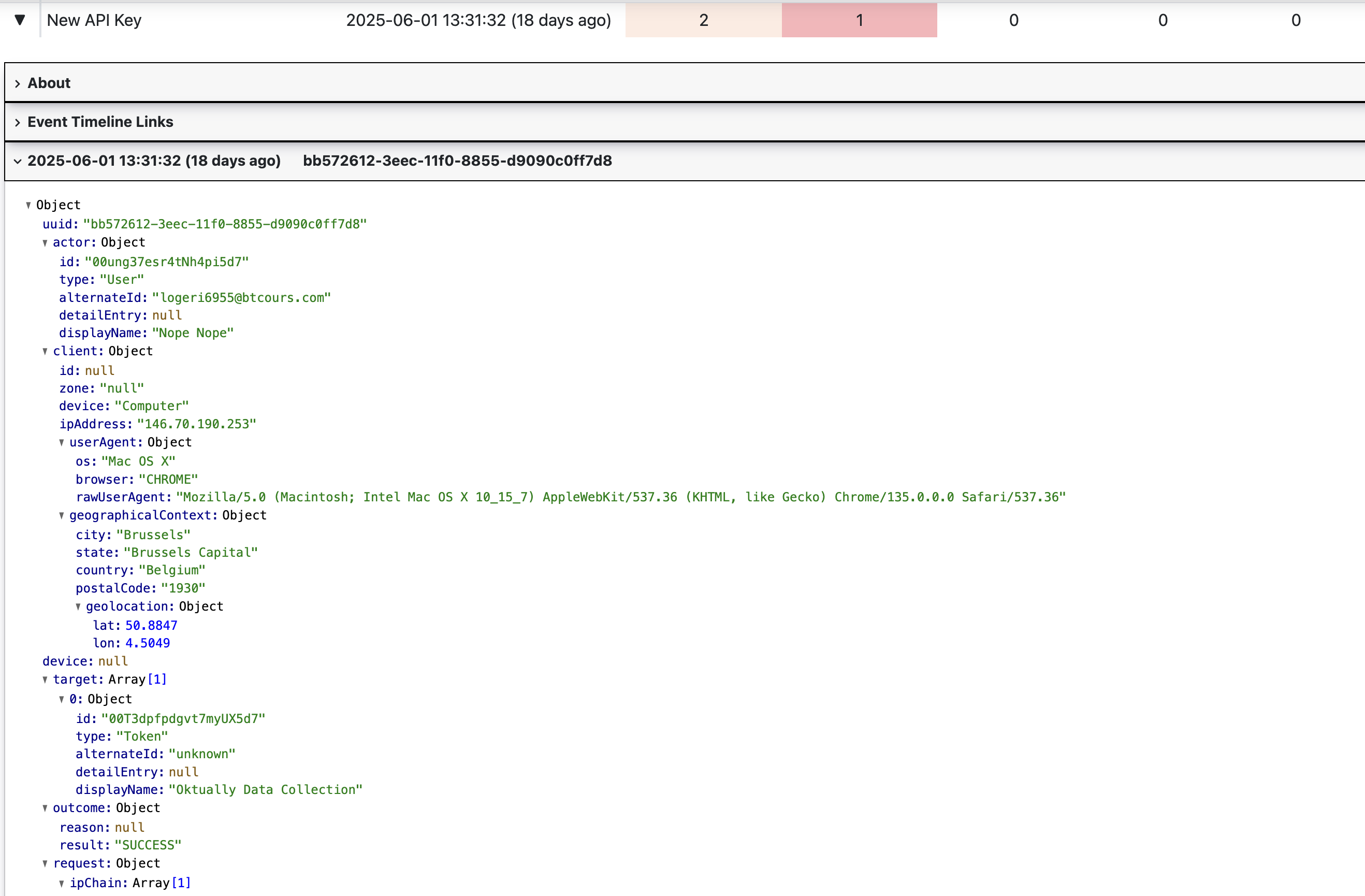
Table Data
Each row represents a separate detection that searches your Okta log and counts detected events in the last 90 days.
Latest shows the timestamp of the most recently detected event. Each of the # Last X Days columns show the number of detected events from a window of today, backwards X days. # Last 90 Days is therefore the total number of detected events in the last 90 days, if ...90 days and ...45 days both have a value of 1, there has only been one event detected but it happened within the last 45 days.
The Last X columns provide a sense of both scale & recency. With event based detections, recent events tend to be of more interest and are easier to investigate whilst their related context is fresh.
Missing Required Field(s)
When a detection is Missing Required Field(s), Oktually was unable to find a required data field in your Okta tenant to run the detection. This can happen for the following reasons
- The log fields required for the detection do not appear unless you’ve purchased & configured a particular license for Okta
- You need to add a specific field to the Okta group or user profile, so the detection can use that field to filter events
Open the About section of a detection to see any field requirements.
Note that missing a complete field of data and missing specific event types are different situations. It is impossible to detect from the log alone when a specific event type is missing, because it can’t be proved whether the absence is due to a missing license or the event having not occured yet.
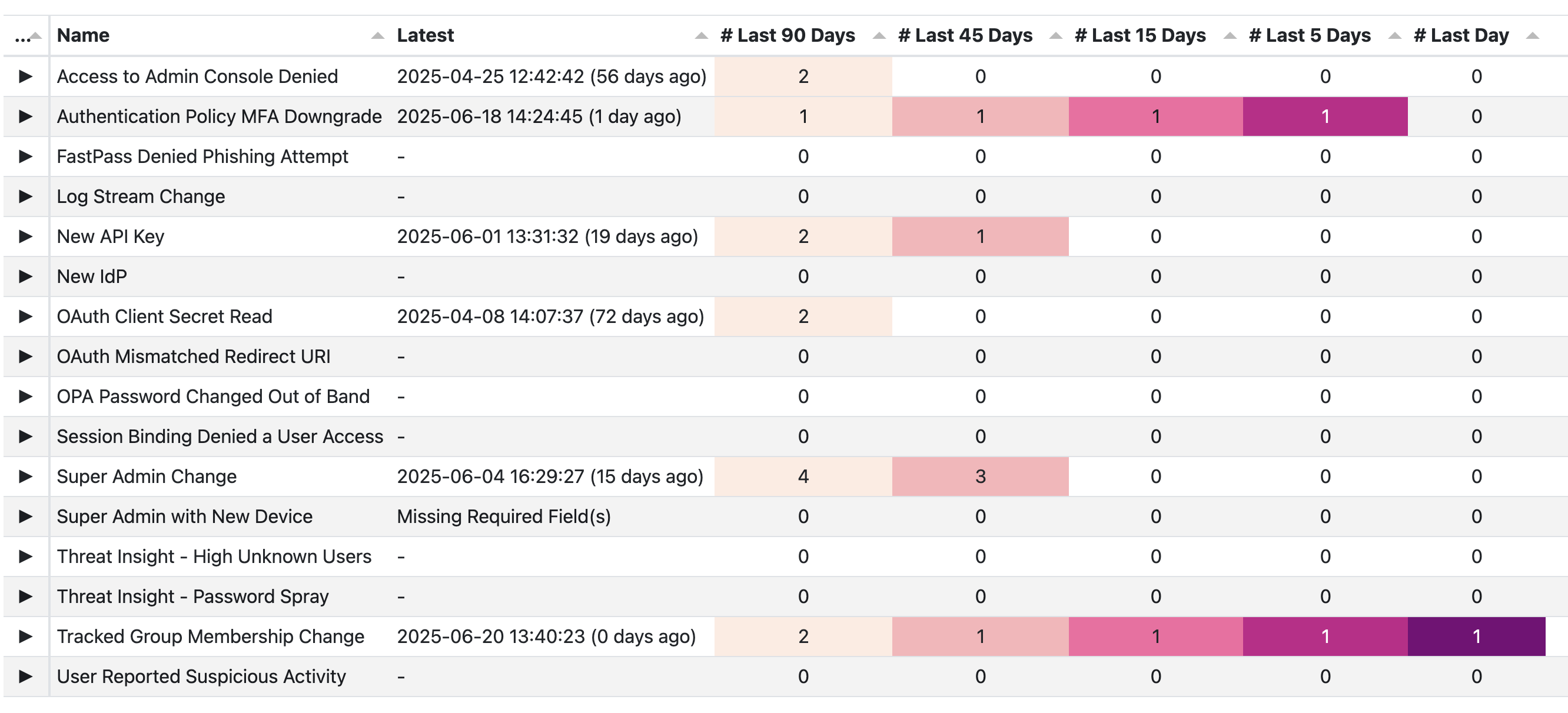
Current Detections
- Access to Admin Console Denied
- Authentication Policy MFA Downgrade
- FastPass Denied Phishing Attempt
- Log Stream Change
- New API Key
- New IdP
- OAuth Client Secret Read
- OAuth Mismatched Redirect URI
- OPA Password Changed Out of Band
- Session Binding Denied a User Access
- Super Admin Change
- Super Admin with New Device
- Threat Insight - High Unknown Users
- Threat Insight - Password Spray
- Tracked Group Membership Change
- User Reported Suspicious Activity
Detection Sources
Inspiration for detections comes from external sources and the experience of Oktually’s Engineer. Sources are provided when used; if there’s no Source in the About section, the detection was developed by Oktually.