Admin Downgrade
Motivation
- Keeping admin permissions appropriately scoped and not constantly expanding is a constant task for Okta admins
- JIT admin permissions and automated processes for acquiring & revoking admin permissions are the ideal situation, but many orgs struggle to find time & buy-in to implement these solutions
- The Admin Downgrade insight gives you a consistently applied methodology to follow, that will help keep admin creep under control
Basic Usage
- Open up the
Admin Downgradeapp - Recommendations for your Okta admins are in light yellow expandable bars, click on one
- With caution, follow the recommendation. For an explanation read the rationale
- Watch as your number of overpowered admins drops over the coming days & weeks!
Tips for Cautious Use
- If the admin you’re downgrading is a service account, consult the documentation for that service. If none is available, the creator of the service may be able to help
- If Oktually recommends downgrading many admins, work slowly. You can downgrade single or small groups of admins and wait a few days before downgrading more. Aim for “gradually better”, rather than “FIX IT NOW”
- Caution does not mean you have to inform every user whose admin permissions you’re downgrading. Oktually recommends making users aware that unused admin permissions will be revoked and then taking silent action when required. If you ask every user before a downgrade, they’ll inevitably claim to still need the access; you have the data, trust it!
Admin Downgrade Path
When downgrading admins, keeping to a standardized path helps manage expectations about how admin permissions change over time. Recommendations within this insight follow the path below, allowing 72 hours between recommendations to see if admins at a new “step” in the path take action to justify them staying there.
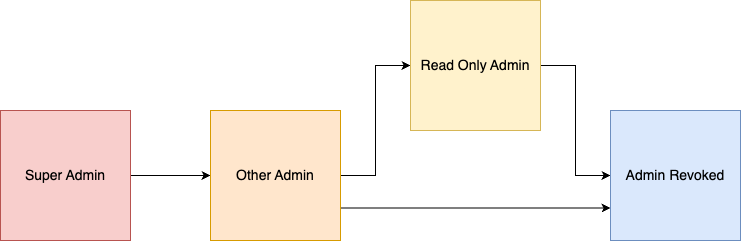
The recommendation engine is designed to encourage slow but consistent change in admin permissions. In the extreme case, the shortest possible timescale for downgrading from Super to Revoked is 9 days*. Assuming you downgraded the admin as soon as Oktually recommended each time, and the user with admin permissions did nothing an admin would (no admin UI sign-in, admin actions or API key).
The period of activity assessed after each 72 hour wait is much longer (30-90 days), so admins don’t have to be using their permissions every 72 hours!
*9 days because Oktually would wait 72 hours after the initial granting of Super Org Admin, then another 72 hours after each subsequent step down the path. One initial wait period, plus two transitions (to Other Admin, then Revoked) means three 72 hour periods = 216 hours, or 9 days.
Recommendations
This insight currently supports the following recommendations, each based on data from your Okta Workforce tenant
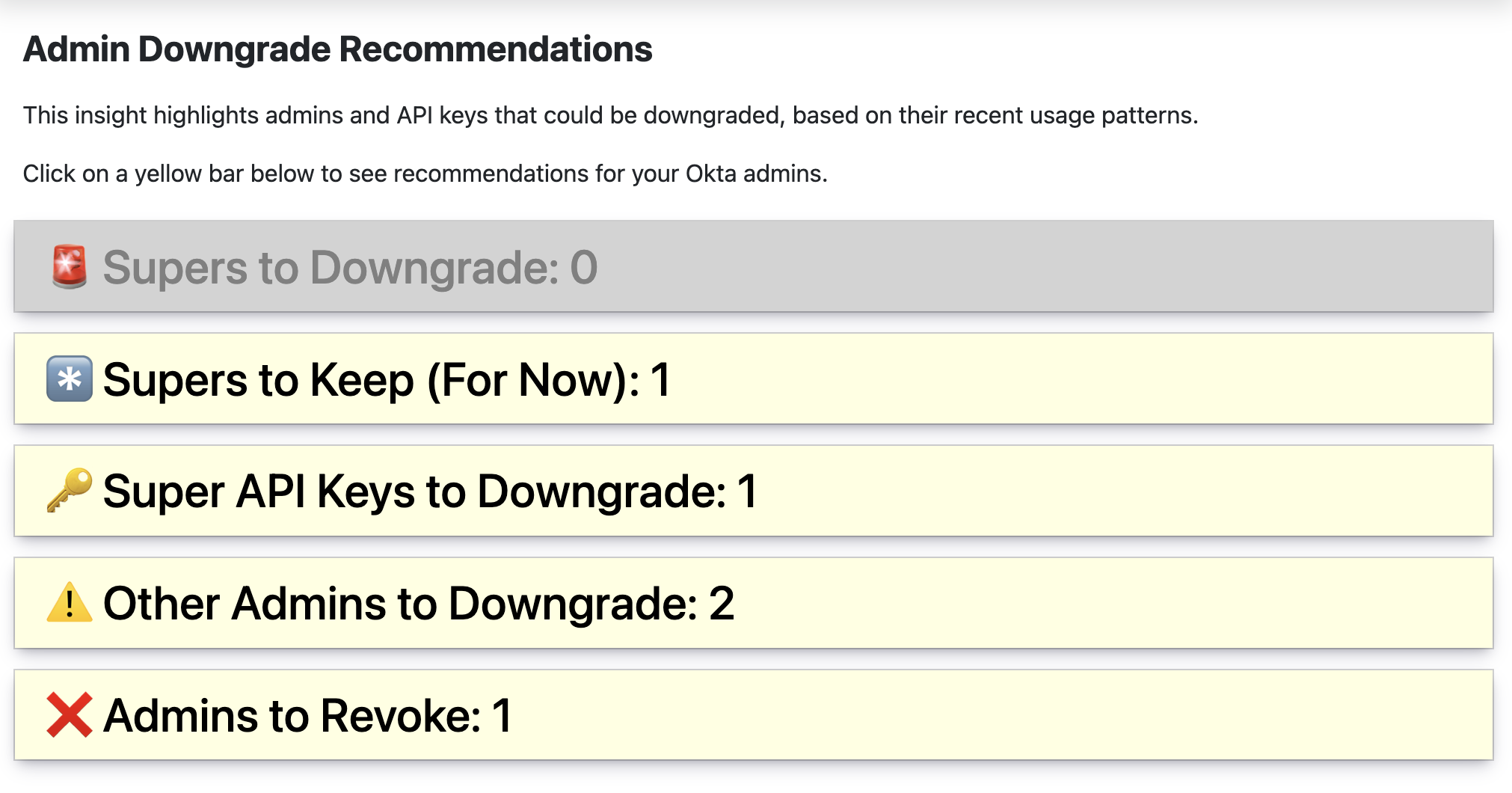
Supers to Downgrade
Users who have not taken any actions in Okta within the last 30 days that clearly require them to be Super Admins.
Supers to Keep (For Now)
Super Admins who would ordinarily be recommended for downgrading, but Oktually recommends keeping them in order to meet a lower limit of Super Org admins.
When Oktually chooses between two admins who would both normally be recommended for downgrading, it chooses the older account to keep, on the assumption that user has more business specific context.
Super Admins who have been triggering known Super Admin events will not appear here.
Super API Keys to Downgrade
A Super Admin API key offers complete control over your Okta instance including the ability to remove other Super Admins, their existence should be avoided at all costs (even IP limited).
Extremely narrow use cases involving automating admin permissions do exist, but would be better served via a backend services app with Super Org Admin permissions and the okta.roles.manage scope.
Other Admins to Downgrade
Non-Super Admins have signed into the admin dashboard or have an API key, but they have not taken any CUDAR actions in the last 30d.
CUDAR stands for Create, Update, Delete, Add, Remove — admin changes usually result in firing an event containing one of these verbs, reading data via the admin UI or API does not.
Admins to Revoke
Non-Super Admins have not signed into the Admin dashboard within the last 90 days and don’t have an active API key; meaning they haven’t used their admin privileges in at least that long.
Super Admin Philosophy
For more on the philosophy behind managing Okta Super Admins in particular, check out this series of posts on the Oktually blog